Article • Cybersecurity in hospitals
Ransomware: The race between attackers and defenders
Among a multitude of threats to hospitals‘ IT infrastructures, ransomware was a niche phenomenon until circa 2015. Since then, the number of known ransomware attacks has not only increased substantially across many industries. Hospitals, and the healthcare industry in general, have also become favorite targets of ransomware attackers, leading to very real incidents in which patient care and patients’ lives have been put at risk.
Report: Dr Christina Czeschik
Taking data hostage
Ransomware is a type of malware that is based on public key encryption. This technology is in itself an important building block of information safety and security: it allows for very secure encryption of data and is used, for example, in encrypted e-mail and in digital signatures.

Image source: Gino Crescoli from Pixabay
In public key encryption, a user digitally generates a set of keys, consisting of a public and a private key. These have an important mathematical property: Data encrypted with the public key can only be decrypted with the private key, and vice versa. Encryption with the public key and decryption with the private key is the standard procedure when public key encryption is used for the safekeeping of data.
In benign applications of public key encryption, such as email encryption with S/MIME or PGP, the public key can be made public, as the name suggests, on key servers and through other modes of communication. The private key will be kept safely by the key pair owner, as access to the private key would allow anyone to decrypt his or her confidential messages or data.
This central role of the private key is exploited by ransomware: the ransomware program, once it has successfully entered an IT system, will encrypt any data within its reach (i.e., within the network) with a public key. The corresponding private key is kept by the attacker and offered to the victim only in exchange for a substantial amount of money, often to be paid in cryptocurrency to a quasi-anonymous wallet.
To pay or not to pay
In theory, there are three ways of recovering those encrypted data: Paying the ransom and hoping that the attacker will be sufficiently honest to actually deliver the private key; replacing the encrypted data with (hopefully sufficiently current) backups; and decrypting the data without the private key.
The last solution can mostly be discounted: It has worked only in very rare instances in which there were bugs in the ransomware itself. Mathematically, if properly implemented, public key encryption with sufficient key length cannot be broken with today’s computers.
Right from the beginning of known ransomware attacks, authorities all over the world have urged victims to not pay the ransom and instead recover the encrypted data from their previous backups. However, even accounting for unrecorded cases that never find their way into the statistics, the evolution of ransomware into a sophisticated industry proves that enough victims must have paid their ransoms to ensure the profitability of the business model.
Recommended article

Article • Healthcare IT security
Multifactor Authentication: a strong defense, but not impenetrable
IT networks of hospitals and other healthcare institutions are currently very much in the focus of both hackers and IT security specialists. In a healthcare landscape in which both organizational and medical heavily rely on IT, keeping networks safe is key to protecting patients’ data and lives.
Differentiation of business models
Ransomware gangs have now differentiated into franchisers and franchisees, many even offering user-friendly “support” pages helping victims who are not sure how to use cryptocurrency for their payment or run into other practical problems. They have used the Emotet infrastructure (now defunct, but replaced by Qakbot and others) to distribute their malware in personalized, seemingly trustworthy email messages. Some ransomware even infiltrates the network stealthily and injects false data into databases to make backups useless and thus force victims even more strongly to pay the ransom. Others enforce their ransom demands by threatening to publish the victim’s data, such as the Ragnarok gang in July and August 2021.
Law enforcement catching up
However, the Ragnarok gang and others, such as the developers of the Ziggy and Avaddon malware, respectively, have recently given up and published their private keys on their websites. Victims were then able to decrypt their data without resorting to ransom payments. Analysts assume that law enforcement got uncomfortably close to these groups in the wake of the Emotet investigation, motivating them to give up their activities (for now).
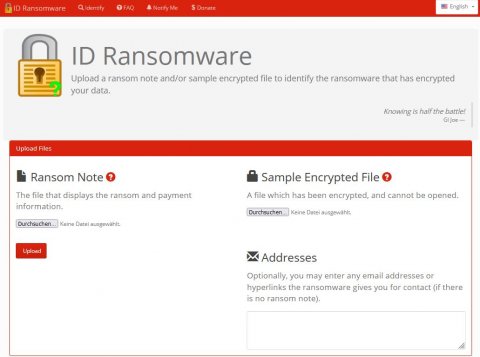
IT security specialists recommend victims of such defunct groups to wait for decryption tools from legitimate sources rather than using the tools provided by the groups themselves. Examples for legit tools are ID Ransomware and No More Ransom. Both are regularly updated with new keys and the latter is co-founded by the European law enforcement agency Europol.
At the same time, prevention and risk management of ransomware attacks is also increasingly coming into the focus of IT security specialists. For instance, the Israeli cybersecurity firm Guardicore recently added a ransomware simulation to their open source pentesting tool Infection Monkey, available at https://github.com/guardicore/monkey.
07.10.2021