Image source: Unsplash/FLY:D
Article • Healthcare IT security
Multifactor Authentication: a strong defense, but not impenetrable
IT networks of hospitals and other healthcare institutions are currently very much in the focus of both hackers and IT security specialists. In a healthcare landscape in which both organizational and medical heavily rely on IT, keeping networks safe is key to protecting patients’ data and lives.
Report: Dr Christina Czeschik
An important building block of network security is identity and access management (IAM): only legitimate users can be granted access to sensitive systems. IAM has moved from simple user name and password combinations in its earliest days to what is now called multifactor authentication (MFA): supposedly legitimate users must authenticate themselves, i.e. prove their identity, using a combination of factors. While certainly more secure than the old one-factor authentication based on passwords only, MFA has its weaknesses too, as IT security specialist Roger Grimes of KnowBe4 recently demonstrated in his HIMSS webinar, “Hacking Multifactor Authentication: An IT Pro’s Lessons Learned After Testing 150 MFA Products“. The webinar was originally held on August 17 and is accessible on demand via this link.
Three classes of authentication factors
In most healthcare organizations, MFA is currently implemented as 2-factor authentication (2-FA), meaning that users need to present two factors, i.e. pieces of evidence to prove their authentication to the system. These factors may fall into any of the following three categories:
- Something the user knows (e.g. a PIN, password or passphrase)
- Something the user has (e.g. a token or smartphone)
- Something the user is (e.g. a biometric feature such as a fingerprint)
Each of these classes of authentication factors come with their own challenges. Knowledge can be forgotten, items can be stolen, even biometric features can be faked. Combining two or more increases the security of a system substantially.
Usable and useless multifactor authentication
People do not like to be bothered by security. People just want to do their job
Roger Grimes
However, as Grimes points out, MFA systems designed to resist more and more sophisticated attacks run the risk of becoming unusable. He cites the example of security companies offering authentication schemes in which users are required to enter their PIN on a virtual keypad with continually changing number placement, to prevent attackers decoding PINs based on greasy fingerprints that users leave on often-used numbers. Another example are schemes that require users to solve mathematical riddles according to a private code table (hopefully) not accessible to attackers.
While good in theory, Grimes predicts that authentication methods like these will never gain widespread user acceptance due to their lack of usability. If users have to put up with authentication procedures at all, they prefer the quick and easy way. In Grimes’s words: “People do not like to be bothered by security. People just want to do their job.”
There is probably no field for which this statement sums up the attitude towards IT security as accurately as for the healthcare sector.
A multitude of ways to crack MFA
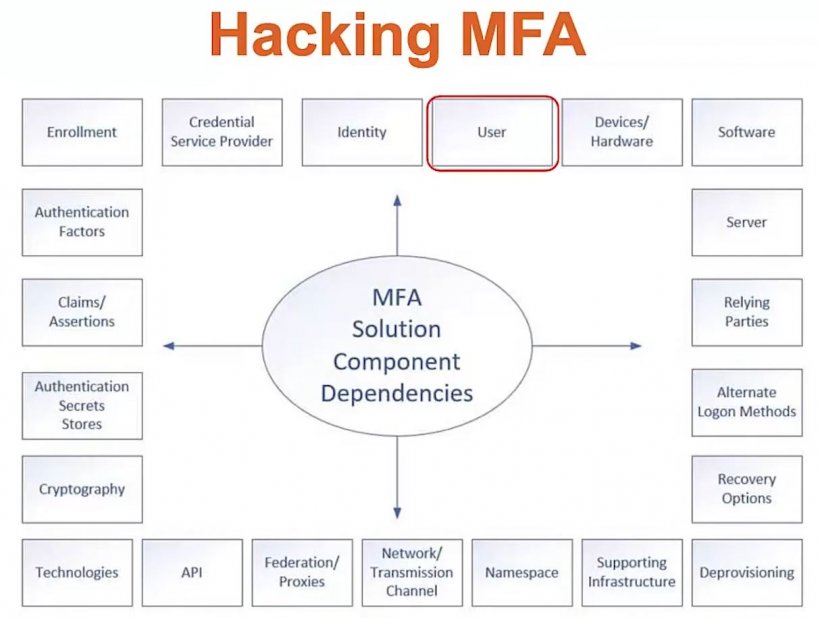
So, how is it possible to design an attack-proof MFA system using only easy-to-use factors? The answer according to Grimes: it’s not. As he emphasizes repeatedly, all MFA systems are hackable. The potential weaknesses can be identified using a threat-modeling methodology, in which components of the system and their dependencies are visualized and analyzed (see figure).
In general, only a fraction of successful attacks really do hack the MFA procedures themselves. The most dangerous (or useful, depending on your point of view) approach is social engineering, in which the attacker fools legitimate system users or even administrators into giving him or her access, or at least inadvertently disclosing sensitive information that can be used to gain access.
Other approaches to hacking MFA include illegitimately using recovery or bypass mechanisms (such as procedures for lost passwords or tokens), insecure reset-to-default procedures, exploiting programming bugs in software components that have not yet become public and thus not yet been patched by the manufacturer, and a multitude of others.
Grimes’s company offers an online questionnaire-based tool to assess individual systems’ vulnerabilities, available at https://www.knowbe4.com/multi-factor-authentication-security-assessment along with other free security tools and tests.
Security awareness is key
In summary, MFA does not provide perfect security (and neither do any other defense systems in the digital world). IT security is thus always a matter of risk management: the most likely attack vectors and most fatal vulnerabilities must be addressed first. In the case of MFA systems, the biggest lever to improve security is to improve users’ security awareness, i.e. educating and training them to avoid dangerous behavior.
This is easy and hard at the same time – easy because one person can modify their behavior right away, without huge financial overhead or long project timelines. Hard because changing human behavior within an organization, permanently and sustainably, requires resources and a lot of commitment.
16.09.2021