Patient Safety
Expert highlights hospitals vulnerability to hacks
Is your network safe? This loaded question made delegates shiver during Inforsalud 2015, the annual meeting of the Spanish Health Informatics Society, which was held Feb 17 - 18 in Madrid.
Report: Mélisande Rouger

In a fast-paced, hectic presentation, Dr Jesús Díaz Barrero, systems engineer at Palo Alto Networks (PAN), highlighted how hospitals are increasingly the target of advanced persistent threats (APTs) – groups with both the capability and intent to persistently and effectively target a specific entity.
Over the past few years, an increasing number of cases have been reported in which hackers modified the parameters of an insulin bomb or a defibrillator, to deliver random shocks to a patient’s heart from the Internet. Recently, a report stated APTs from the Chinese army stole millions of personal data from US hospitals (1) and (2).
The reason is simple: it is incredibly easy to hack a hospital. Millions of players can access a hospital’s network, either outside or inside the facility. For instance, patients can consult their reports and interact with their doctors from home.
These new means of communication increase the possibility of APTs, according to Díaz. “Each time we open a door, we find a problem,” he said. The growing use of telemedicine in Spain, especially in remote areas such as Balearic Islands, also increases this risk. So does access to the network by external clinics, delegations, manufacturers, pharmaceuticals and insurance companies, lawyers, etc.
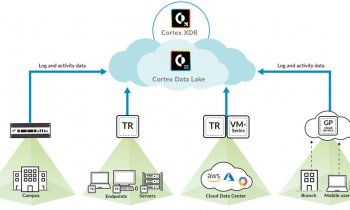
Within the hospital or campus, many teams are connected to the network – labs, examination rooms, patient rooms, and so on and so forth. Even the private WAN (3), which connects all medical systems like PACS and information exchange systems, can be a target.
“Having all these channels means that the opportunity for an APT is very high. I don’t want to scare you, but this is the reality of the healthcare setting today all around the world including Spain. We are used to thinking that bad things only happen elsewhere. You’ll see how it is far from being the case,” he said.
He presented studies conducted near 3 randomly chosen healthcare facilities over a year, which showed how vulnerable these facilities were. All of them emitted malware from their own network without being aware of it. Malware, short for malicious software, is hidden within standard web content and designed to exploit vulnerabilities on Internet-enabled applications, such as browsers and browser plug-ins. Its aim is to disrupt computer operation, gather sensitive information, or gain access to private computer systems.
Researchers placed external waves to monitor web traffic at those facilities. Results show that not only did scanners, modems and web cams emit malware, but also radiology systems and, most surprising of all, firewalls. “Firewalls are supposed to protect hospital systems against malware, but they were actually the main source of malware. More alarmingly, the staff responsible for the system security did not know what was going on,” he said.
PAN gathered information over the past five years at a large number of facilities and healthcare companies in Spain. The firm found out that all of the amenities had malware in their systems. They all shared the same problem: their security systems did not work together, Díaz pointed out. “The facilities failed because of dispersion. Traditionally, we’ve put punctual solutions that work independently and are not related to each other. So when I have an incoming threat, I am getting lost in this mess. It’s also crucial to distinguish which threat is important and which isn’t. Moreover, most security systems need manual intervention, which is time consuming,” he said.
He recommends hospitals to correlate information between their systems and identify what applications they have in their networks – and decide whether they are safe or not. Information should be segmented, and access to the server should be granted strictly and according to the visitor’s needs.
Hospitals should also apply the 0 Trust principle, in which two critical machines cannot share the same level of security. Access from one to the other should be protected, for instance by passwords. With the explosion of smart phones and tablets use, one should also adapt these measures to the mobile world. Last but not least, a security platform should be able to counter both known and unknown APTs. Many firms currently offer protection platforms against all sorts of APTs, including Dell SonicWALL, NETGEAR, WatchGuard and PAN. The product PAN-OS is considered an industry leader but recently scored lower on independent NSS Labs test. (4)
(1) www.technologyreview.com/news/530411/hackers-are-homing-in-on-hospitals/
(2) www.cnbc.com/id/101927433.
(3) A wide area network (WAN) is a network that covers a broad area (i.e., any telecommunications network that links across metropolitan, regional, national or international boundaries) using leased telecommunication lines.
(4) www.reuters.com/article/2014/09/26/us-palo-alto-firewall-idUSKCN0HL28U20140926
22.04.2015